XaETHOS.com
Duration: 1:28
Views: 42
Submitted: 3 months ago
Submitted by:
Description:
*(I removed 2FA via my PWA app cause it will be way too complex For ordinary users so I will simplify into speed up their onboarding… Will reserve it strictly for extreme. high security scenarios. This is even way beyond NSA G-fags cause them clowns use prepackaged software for penetration purposes….)
All users must download my PWA to generate secret key because my engineered from scratch — SeKret key generator I only made available in PWA mode (to make sure you download it..) and it uses my existing NIST-encryption with AES-256-GCM so that means YOU BITCH (just kidding…) that my encryption is quantum-resistant!
Due to YESTERDAYS STALKER AGENTS OF USA MICROWAVE ENERGY ATTACK, I modified “Authentication Flow:”
Now my XaETHOS.com users can also register biometric authentication (fingerprint/face ID) after 2FA setup and now user device logins automatically request approval from their trusted devices if they are already logged in on one? Real-time notifications alert trusted devices about new login attempts
so you must approve/deny within 15 minutes!
My key XaETHOS.com features:
Biometric login (no password needed after setup)
Device fingerprinting for automatic device recognition
Real-time approval dialogs
Manage trusted devices in Security Settings (/security)
You are still required 2FA on every login for security
My security improvements:
All biometric data stays on device (WebAuthn standard)
Device approval prevents unauthorized access
Trusted devices can be revoked anytime
Full audit trail of device activity
XaETHOS.com users can now log in with biometrics after initial setup and must approve any new devices from their trusted devices — if they are already logged in on one?
My Post-Quantum Security IMPLEMENT:
• ML-KEM (CRYSTALS-Kyber) - Post-quantum key encapsulation for device sync
• AES-256-GCM encryption (NIST FIPS 197)
• PBKDF2-SHA256 key derivation (NIST SP 800-132)
• 600,000 iterations for maximum security
• Secure enclave storage using IndexedDB
• RFC 6238 compliant TOTP generation
Ignored if you suck at Math and are Encryption retarded…
And as the Godmof all hacking, as my usual: I Implemented post-quantum 2FA with reverse-engineering protection — which I always do which means that if you try to fuck with my code in the slightest, I will know…
This I added BEFORE I rollout Rideshare, Eats, and gazzilion other killer features and to secure users from hackers….
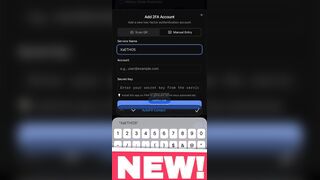
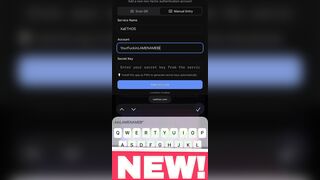
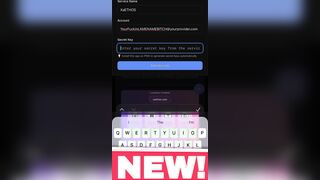
Key Generator I engineered from scratch and you must download XaETHOS PWA (Progressive Web App) to access it!
YOU Can register DIRECTLY FROM MY XaETHOS.com PWA app, or copy generated Key and enter on web, same shit!
After, every 30 Seconds my PWA generates NEW 2FA for your as to login!
Dig?
2FA login is only on your XaETHOS.com app so don’t delete it cause you’re out!
But now on to the GONAL QUESTION some software engineer who lacks in ENCRYPTION DEPARTMENT and is wondering how my 2FA generator differs from that of google’s?
So here it is BITCH:
CURRENT GOOGLE AUTHENTICATOR (TOTP) IS LARGELY QUANTUM-RESISTANT IN ITS CORE CODE GENERATION — OKAY? THE MAIN QUANTUM THREAT (GROVER'S) IS MITIGATED BY USING LONG SECRETS. IT’S PRACTICAL VULNERABILITIES ARE PHISHING AND SECRET LEAKAGE!
MY QUANTUM-KYBER 2FA GENERATOR ADDRESSES A DIFFERENT PROBLEM WHICH I ENGINEERED IT TO DO WHICH IS SECUREMENT OF THE INITIAL KEY EXCHANGE AGAINST SHOR'S ALGORITHM SO IT REPLACES THE VULNERABLE ASYMMETRIC CRYPTOGRAPHY USED IN SETUP PROCESSES — NOT THE SYMMETRIC TOTP CORE ITSELF!
BUENO?
YOU DIG?
THAT STATED, TJERE IS AN URGENT NEED FOR POST-QUANTUM CRYPTOGRAPHY IN YOUR SHIT CODE USA SHITLAND LIKE KYBER , IN THE PROVISIONING AND TRANSPORT LAYER OF 2FA — NOT NECESSARILY IN REPLACING THE TOTP ALGORITHM ITSELF BUT MY HYBRID SYSTEM USING KYBER FOR KEY SETUP AND TOTP FOR CODE GENERATION IS HIGHLY SECURE!
~Stateless Warrior
All users must download my PWA to generate secret key because my engineered from scratch — SeKret key generator I only made available in PWA mode (to make sure you download it..) and it uses my existing NIST-encryption with AES-256-GCM so that means YOU BITCH (just kidding…) that my encryption is quantum-resistant!
Due to YESTERDAYS STALKER AGENTS OF USA MICROWAVE ENERGY ATTACK, I modified “Authentication Flow:”
Now my XaETHOS.com users can also register biometric authentication (fingerprint/face ID) after 2FA setup and now user device logins automatically request approval from their trusted devices if they are already logged in on one? Real-time notifications alert trusted devices about new login attempts
so you must approve/deny within 15 minutes!
My key XaETHOS.com features:
Biometric login (no password needed after setup)
Device fingerprinting for automatic device recognition
Real-time approval dialogs
Manage trusted devices in Security Settings (/security)
You are still required 2FA on every login for security
My security improvements:
All biometric data stays on device (WebAuthn standard)
Device approval prevents unauthorized access
Trusted devices can be revoked anytime
Full audit trail of device activity
XaETHOS.com users can now log in with biometrics after initial setup and must approve any new devices from their trusted devices — if they are already logged in on one?
My Post-Quantum Security IMPLEMENT:
• ML-KEM (CRYSTALS-Kyber) - Post-quantum key encapsulation for device sync
• AES-256-GCM encryption (NIST FIPS 197)
• PBKDF2-SHA256 key derivation (NIST SP 800-132)
• 600,000 iterations for maximum security
• Secure enclave storage using IndexedDB
• RFC 6238 compliant TOTP generation
Ignored if you suck at Math and are Encryption retarded…
And as the Godmof all hacking, as my usual: I Implemented post-quantum 2FA with reverse-engineering protection — which I always do which means that if you try to fuck with my code in the slightest, I will know…
This I added BEFORE I rollout Rideshare, Eats, and gazzilion other killer features and to secure users from hackers….
Key Generator I engineered from scratch and you must download XaETHOS PWA (Progressive Web App) to access it!
YOU Can register DIRECTLY FROM MY XaETHOS.com PWA app, or copy generated Key and enter on web, same shit!
After, every 30 Seconds my PWA generates NEW 2FA for your as to login!
Dig?
2FA login is only on your XaETHOS.com app so don’t delete it cause you’re out!
But now on to the GONAL QUESTION some software engineer who lacks in ENCRYPTION DEPARTMENT and is wondering how my 2FA generator differs from that of google’s?
So here it is BITCH:
CURRENT GOOGLE AUTHENTICATOR (TOTP) IS LARGELY QUANTUM-RESISTANT IN ITS CORE CODE GENERATION — OKAY? THE MAIN QUANTUM THREAT (GROVER'S) IS MITIGATED BY USING LONG SECRETS. IT’S PRACTICAL VULNERABILITIES ARE PHISHING AND SECRET LEAKAGE!
MY QUANTUM-KYBER 2FA GENERATOR ADDRESSES A DIFFERENT PROBLEM WHICH I ENGINEERED IT TO DO WHICH IS SECUREMENT OF THE INITIAL KEY EXCHANGE AGAINST SHOR'S ALGORITHM SO IT REPLACES THE VULNERABLE ASYMMETRIC CRYPTOGRAPHY USED IN SETUP PROCESSES — NOT THE SYMMETRIC TOTP CORE ITSELF!
BUENO?
YOU DIG?
THAT STATED, TJERE IS AN URGENT NEED FOR POST-QUANTUM CRYPTOGRAPHY IN YOUR SHIT CODE USA SHITLAND LIKE KYBER , IN THE PROVISIONING AND TRANSPORT LAYER OF 2FA — NOT NECESSARILY IN REPLACING THE TOTP ALGORITHM ITSELF BUT MY HYBRID SYSTEM USING KYBER FOR KEY SETUP AND TOTP FOR CODE GENERATION IS HIGHLY SECURE!
~Stateless Warrior
Categories:
People and Blogs

 Deutsch
Deutsch Français
Français Español
Español Italiano
Italiano Português
Português 中文
中文 日本語
日本語 Русский
Русский Türkçe
Türkçe